
Benefits of Cybersecurity through Giacom

Curated portfolio designed for SMBs
Our portfolio is designed for MSPs and SMBs, with solutions that complement and layer to offer excellent cyber defence against criminals.

In-house Security Practice
Our in-house cybersecurity specialists are ready to support you through the full sales cycle across our portfolio.

SLAs with Tech Support
Our tech Support team boasts 97% of cases resolved within SLA, with the majority resolved in-house too!

Security business review
Schedule a cybersecurity business review with a Giacom specialist, and we’ll walk you through the solutions you should be taking to market, and how to do so.

Clear communication
We know cybersecurity is full of acronyms, so we keep it simple. Using clear, common language ensures all Channel providers work toward the same goal without confusion.

Thought leading content
Our ‘Cyber Security Newsletter’ is released monthly, with engaging content from us and our vendors. Keep up to date on what’s happening in the cybersecurity market.
Partnering with Giacom to help solve the SMB security challenge
In today’s cybersecurity landscape, SMBs are the most vulnerable in the UK’s digital economy. They rely on tech but often lack the skills and budgets to protect themselves.
We understand the unique needs of SMBs and the crucial role MSPs play in ensuring solid, scalable, and proactive cybersecurity. Through our partner network, we support MSPs with the tools and resources they need to help SMB clients build a strong cybersecurity strategy.
Together, we help SMBs navigate the evolving threat landscape, keeping them protected, resilient, and focused on their core business.

Cybersecurity solutions
Email Security
Often the first line of defence against cyber threats
Email security protects from phishing, malware, and business email compromise. Since email is a common way for cyber criminals to attack, keeping sensitive messages safe is crucial to avoid data breaches.
Vendors: Acronis, Barracuda, Bitdefender, Microsoft, Vade
Endpoint Security
Protecting your business from the ground up
Endpoint security focuses on securing devices like laptops, smartphones, and servers from cyber threats. Every device is a potential weak point, so securing them is key to stopping breaches and protecting your data.
Vendors: Acronis, Barracuda, Bitdefender, Microsoft, OpenText Cybersecurity
Backup & Recovery
Ensuring business continuity in the face of disaster
Backup & recovery solutions regularly copy and securely store your data. This is essential for recovering from cyberattacks, hardware failures, or natural disasters, ensuring your business runs smoothly.
Vendors: Acronis, Barracuda, Microsoft, SkyKick
Network Security
The backbone of a secure digital environment
Network security keeps infrastructure safe from unauthorised access, cyberattacks, and data breaches. Tools like firewalls, intrusion detection systems, and VPNs help protect data, ensuring smooth operations without disruptions.
Vendors: Acronis, Bitdefender, Barracuda, Microsoft
Human Risk
Turning your workforce into cyber security champions
Human risk management addresses vulnerabilities caused by phishing and social engineering. Since human error often leads to breaches, training and awareness programs are crucial to reducing these risks.
Vendors: Acronis, usecure, OpenText Cybersecurity
Mobile Security
Securing mobile devices in a connected world
Mobile security protects smartphones, tablets, and other portable devices from cyber threats. As more people use mobile devices for work, securing them is vital to prevent data breaches and unauthorised access.
Vendors: Bitdefender
Threat Detection & Response
Rapidly identify & mitigate cyber threats
Threat Detection and Response (TDR) uses AI and machine learning to spot and stop threats in real time. By constantly monitoring networks, systems, and endpoints, TDR quickly identifies dangers, minimises damage, and protects critical data.
Vendors: Acronis, Barracuda, Bitdefender, Microsoft
0%
of UK businesses experience breaches or attacks at least once a week*
0%
of SMBs have experienced a cyber attack in the last 12 months*
0%
of successful cyber attacks come from phishing and human error*
*Cyber Security Breaches Survey 2024
Interested in reviewing your Cybersecurity strategy?
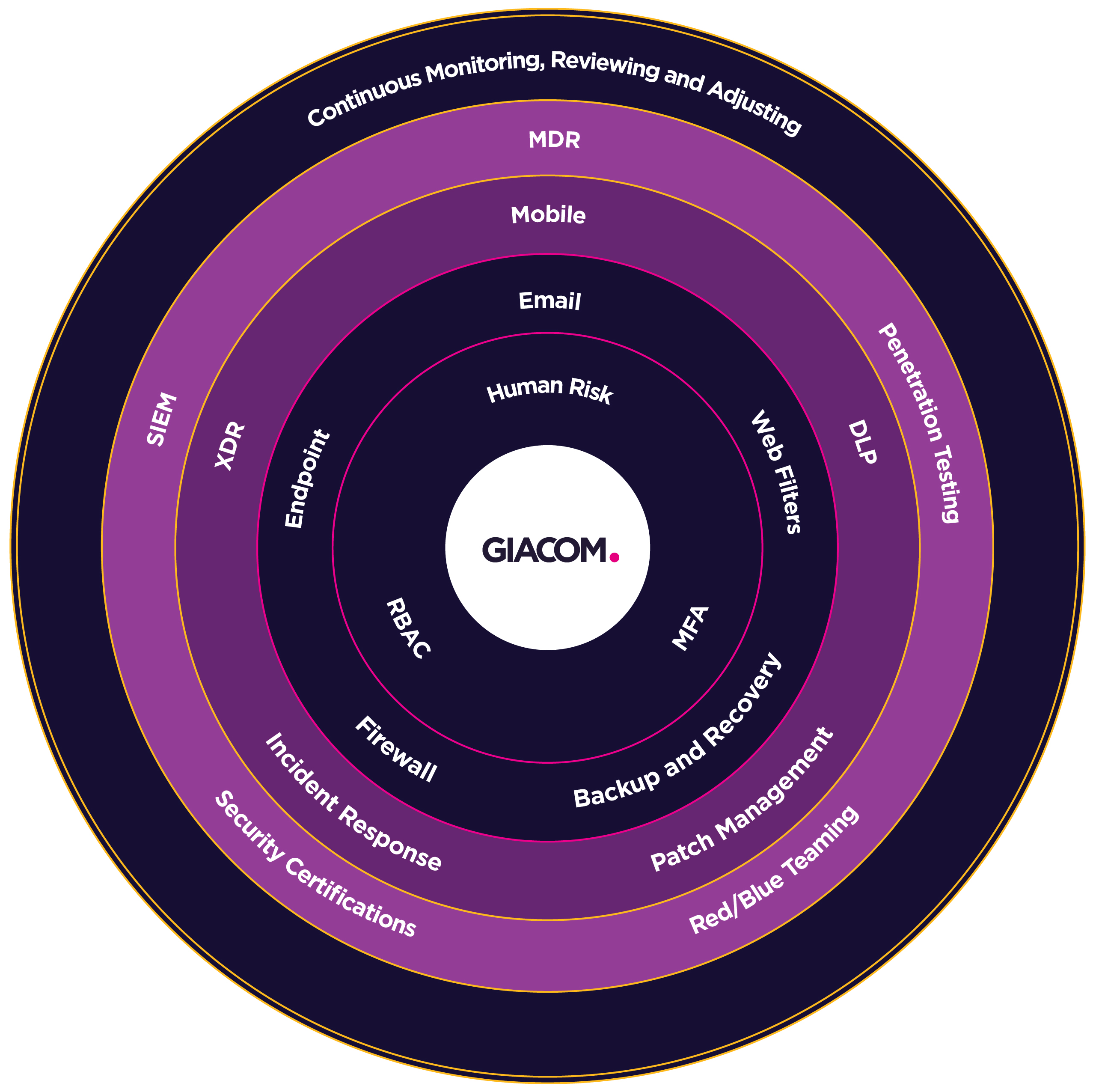
Giacom Security Framework
The Importance of Framework Alignment
Cybersecurity is constantly evolving, but staying ahead of threats doesn’t have to be complicated.
Our framework allows to relay product recommendations and best practices to any SMB customer without needing specialist knowledge. Layer solutions shown in the graphic opposite and make the cybersecurity journey clear and costs predictable. You can suggest scalable solutions based on your customer's budget and needs, ensuring they have a solid base layer of protection that can be enhanced as needed.
Want to know more? Speak to one of our specialists who can walk you through our framework.
Interested in our Security solutions?
Sign up with Giacom to get instant access to:
- Comms, Cloud, Billing and Hardware through a single innovative digital platform.
- The UK’s most comprehensive portfolio of technology products & services.
- Award-winning service delivered by a passionate in-house team.
FAQs
- Why is cybersecurity important for an SMB?
- What are the most common cyber threats to SMBs?
- How can I protect my business from cyber threats?
- What should I do if my business experiences a cyber attack?
- How often should I update my cybersecurity measures?
- How can I ensure my employees are aware of cyber security best practices?
- Do I need a dedicated cyber security team?
- What is a cybersecurity policy, and why do I need one?
- How can I recover from a cyber attack?
- What is the difference between a virus and malware?
Cybersecurity is crucial because SMBs are often targeted by cyber criminals due to their perceived lack of robust security measures. A successful cyber-attack can lead to financial loss, reputational damage, and legal consequences.
Common threats include phishing attacks, ransomware, data breaches, malware, and insider threats. These can disrupt operations, steal sensitive information, and cause significant financial harm.
Implementing multi-factor authentication (MFA), enforcing strong passwords, and maintaining good digital hygiene is a great place to start. From here, align to a framework that suits as this will ensure all bases are covered. We can recommend a few to check out, as well as our own!
Immediately isolate affected systems, notify the IT team, or cybersecurity provider, and report the incident to relevant authorities. Conduct a thorough investigation to understand the breach journey and prevent future incidents. Having a team of experts at hand on retainer is a great peace of mind.
Regularly update your cybersecurity measures, including software patches and security procedures. Conduct periodic risk assessments and vulnerability scans to stay ahead of potential threats. Keep updated on market trends to stay ahead of emerging threats.
Provide regular training sessions on recognising phishing emails, safe internet practices, and the importance of strong passwords. Encourage a culture of security awareness within the organisation. For enhanced employee awareness adopt a formal training procedure which stays aligned to the market and emerging threats.
While having a dedicated team has its benefits, partnering with a 3rd party is a better decision financially as they will already hold the latest certifications and be up to speed on the industry trends and procedures. Doing this independently may be a costly investment, but it’s suitable for some companies. Speak to a specialist to learn more!
A cybersecurity policy outlines the rules and procedures for protecting your business's digital assets. It helps ensure consistent security practices and provides a clear framework for responding to incidents. Employees should agree to this policy and commit to being vigilant with incoming emails, phone calls and other avenues for a cyber criminal to get in.
Having a robust data backup and recovery plan is essential. Regularly back up critical data and test your recovery procedures to ensure you can quickly restore operations after an attack. Having an expert on retainer for this service is a great idea, as they will be able to get you back up and running with minimal disruption.
A virus is a type of malware designed to replicate and spread to other computers, often causing harm and making endpoints unusable. Malware is a broader term that includes viruses, worms, trojans, ransomware, and spyware.
